Opcito Technologies inaugurates its new Pune office
The new state-of-the-art India Development Centre perfectly reflects Opcito's brand ethos and was inaugurated in a dazzling ceremony by Dr. Sunil Patil, former Director of Symbiosis.

Vulnerability scanning for maintaining compliance and regulations
Vulnerability scanning's ultimate goal is to safeguard sensitive data. It is a critical component of any security strategy, enabling you to proactively identify and mitigate security vulnerabilities before they are exploited. The WannaCry ransomware attack of 2017, which affected 230,000 computers and crippled businesses worldwide, is an example of the consequences of neglecting vulnerability management. That's the reason why compliance regulations mainly exist.
The five DevSecOps anti-patterns you must avoid
You might be wondering why we need to talk about anti-patterns when we could discuss the patterns. Think of it this way: Anti-patterns are like the "-5" of the process. If non-DevSecOps practices are a "0," we're not even at neutral yet. Anti-patterns are like taking a wrong turn on a hiking trail. While you may eventually find your way back, you'll waste more time and energy than if you had avoided that detour. We first must stop the bad habits (anti-patterns) before adding real value.
React 17 vs 18 vs 19 – What’s the difference
If you're still using React 17 or 18 for your projects, it might be time to consider an upgrade. React 19 has brought a wave of exciting new features and performance improvements to the table. In this blog, we'll dive deep into the key differences between React 17, 18, and 19. From performance enhancements to new APIs and features, I'll help you understand why upgrading to React 19 could be a game-changer for your development workflow.
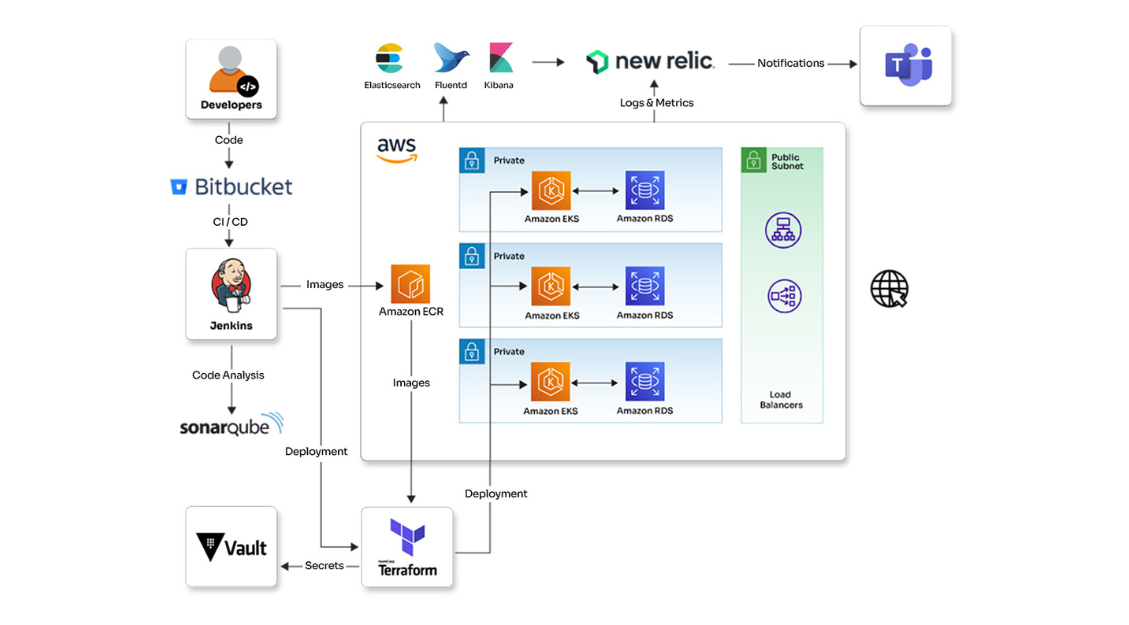
Guide to upgrade an EKS cluster from 1.29 to 1.30 using Terraform
It's time to upgrade your EKS clusters! Following up on my previous blog about upgrading an EKS cluster from 1.28 to 1.29, this highly anticipated Kubernetes 1.30 release, nicknamed Uwernetes, brings new features and improvements. If you're worried about navigating the upgrade process alone, don't worry. This blog will guide you through a smooth and efficient upgrade using Terraform, ensuring your workloads transition seamlessly into the Uwernetes era.
AI-driven vulnerability scanning: A new era of cybersecurity
In a world where cyber threats are evolving rapidly, the practice of vulnerability scanning is undergoing a transformative revolution. Static defences and reactive measures are no longer efficient to discover threats. Today cybersecurity is being shaped by cutting-edge artificial intelligence and machine learning technologies. Just think about the infamous Equifax breach of 2017, where a single unpatched vulnerability exposed millions of sensitive records.
Blue-green deployment with Amazon ECS
Blue-green deployment is a powerful technique for minimizing downtime and risks during software updates. This method involves maintaining two identical environments, referred to as "blue" and "green." Only one of these environments is live, serving all production traffic at any given time. It involves deploying a new version of your application in an environment that is not currently live, allowing for a seamless transition and minimal disruption to users.
How to choose the right vulnerability scanner for your security needs
Organizations find safeguarding their infrastructure and applications complex as the digital landscape becomes increasingly complicated. Unaddressed vulnerabilities can lead to devastating consequences, including data breaches, operational disruptions, and considerable financial as well as reputation damage. A robust vulnerability scanning program is essential to mitigate these risks and protect your organization's critical assets.
Guide to upgrade an EKS cluster from 1.28 to 1.29 using Terraform
Kubernetes 1.28 introduced several enhancements, including improved network policy performance, extended support for Windows workloads, and advancements in CSI volume management. However, as with all software, it's essential to stay updated for the latest features, bug fixes, and security patches. Kubernetes 1.29 builds upon its predecessor, offering further optimizations, new capabilities, and addressing potential vulnerabilities. The 1.29 release is called Mandala - a symbol of the universe in its perfection.
Opcito appoints Nitin Singhvi as Senior Vice President of Engineering
Opcito strengthens its engineering leadership team with the appointment of Nitin Singhvi.