Simplified monitoring and observability in Google Kubernetes engine
This is how Opcito simplified monitoring and observability in Google Kubernetes engine
Engagement details
The customer is a supply chain and logistics giant with a huge IT infrastructure and applications that involved multiple microservices to cater to its customer base with supply chain-related services. Due to its size, real-time insight gathering, and performance & health monitoring of each microservice got challenging. It got crucial to troubleshoot and locate bugs. There was a need to address resource optimization, ensure cost efficiency, and improve the overall platform performance. Opcito's SecOps experts proposed a comprehensive solution that involved implementing robust monitoring and alerting on a customized GKE dashboard. The alerts were integrated with Slack so that the concerned teams could receive notifications via Slack.
Technologies
- GKE
- Google cloud's operations suite (Stackdriver)
- Prometheus
- Grafana
- Slack
Benefits
- Real-time monitoring
- Improved troubleshooting
- Resource optimization
- Proactive issue detection
- Enhanced user experience
Subscribe to our feed
Improving cloud security and intrusion detection with AWS
This is how Opcito improved cloud security and intrusion detection with AWS for the customer
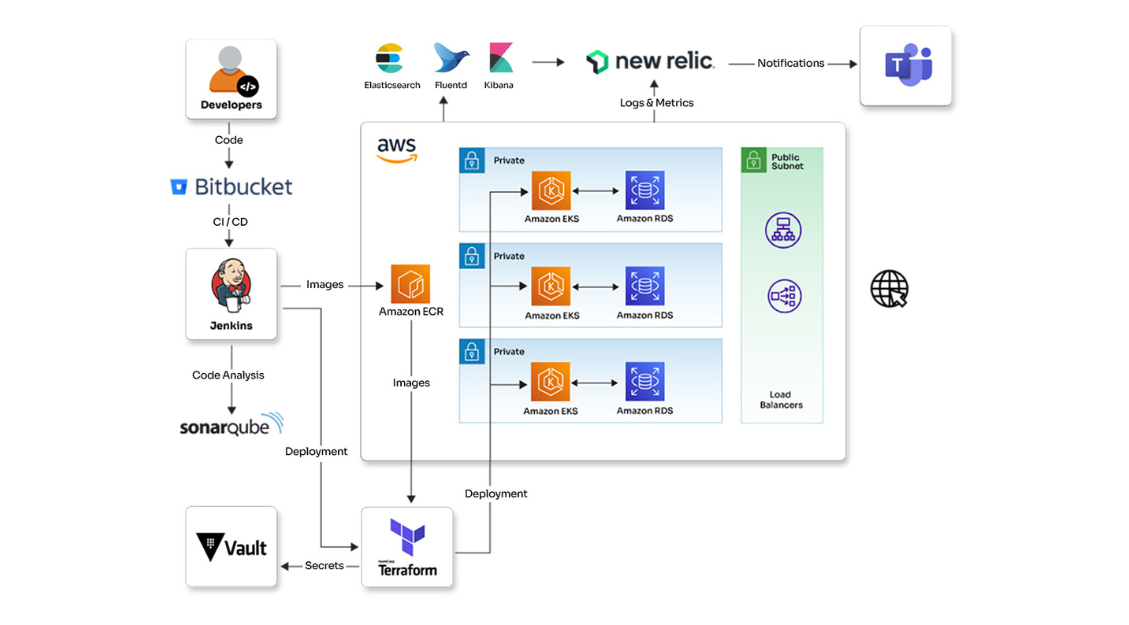
The customer is a FinTech organization that provides various financial services worldwide. With an increasing need for digital services, they decided to transition a significant portion of their operations to the cloud. Due to the large data volumes and sensitivity of proprietary data, it was necessary to own a robust and secure cloud environment. The organization sought a solution that ensured compliance with stringent regulations like GDPR and PCI-DSS, and detect and respond to security threats in real time. They also wanted to minimize human errors in managing configurations and access controls. Opcito proposed a comprehensive solution for infrastructure automation to meet these requirements.
Technologies
- Aws Config
- AWS CloudTrail
- AWS Security Hub
- AWS IAM Analyzer
- Amazon GuardDuty
- Amazon CloudWatch
- Amazon EventBridge
- Terraform
Benefits
- Bolstered security
- Holistic visibility into the AWS environment
- Compliant with GDPR and PCI-DSS
- Proactive threat detection
- Cloud environment expansion possibility
Subscribe to our feed
Enhancing Azure observability for a FinTech ecosystem
This is how Opcito enhanced Azure observability for a FinTech ecosystem
Engagement details
The customer, a fintech leader, helps financial institutions modernize their regulatory landscape. They leverage Azure and related services like AKS, App Services, Storage Accounts, Key Vaults, DNS, Virtual Networks and more to serve the unbanked, streamline operations, and strengthen supervisory decision-making. As the ecosystem grew more intricate, the customer encountered challenges like lack of real-time monitoring, oversight, scalability concerns, immediate issue detection & rectification, and increasing costs. Opcito's SecOps experts devised a comprehensive Azure-focused monitoring strategy that gave the customer an unmatched view of the customer's extensive operations, while providing the customer with a coherent view of their operations.
Technologies
- Azure (Dashboards, Metrics & Diagnostics, Monitor, Insights, Analytics)
Benefits
- Unparalleled oversight
- Adaptable monitoring
- Anticipatory mechanisms
- Improved APM
- Resource efficiency
- Consistent observability
Subscribe to our feed
Enhanced monitoring, logging, APM, and incident management with Datadog
This is how Opcito enhanced monitoring, logging, APM, and incident management with Datadog
Engagement details
The customer provides a monitoring and security platform for cloud applications that brings together end-to-end traces, metrics, and logs to make applications, infrastructure, and third-party services entirely observable, helping businesses secure their systems and avoid downtime. Due to limited insight into their extensive AWS infrastructure and application performance, early detection and quick resolution of complex issues were problematic. The system's growth in scale and the addition of microservices made pinpointing root causes increasingly complex, leading to longer resolution times. Also, consolidating and analyzing log data from various AWS services were scattered and inefficient, impeding timely problem detection and response. Opcito's monitoring experts proposed to integrate Datadog with the customer's AWS infrastructure for detailed performance data and insights.
Technologies
- AWS (RDS, WAF, CloudWatch logs, Kinesis data, Firehose, Lambda, S3 bucket)
Benefits
- Better monitoring
- Enhanced visibility
- Efficient log management
- Improved APM
- Real-time alerts and effective incident management
- Cost optimization
Subscribe to our feed
Nagios for monitoring on-premises infrastructure
See how Opcito used Nagios for monitoring the customer's on-premises infrastructure
Engagement details
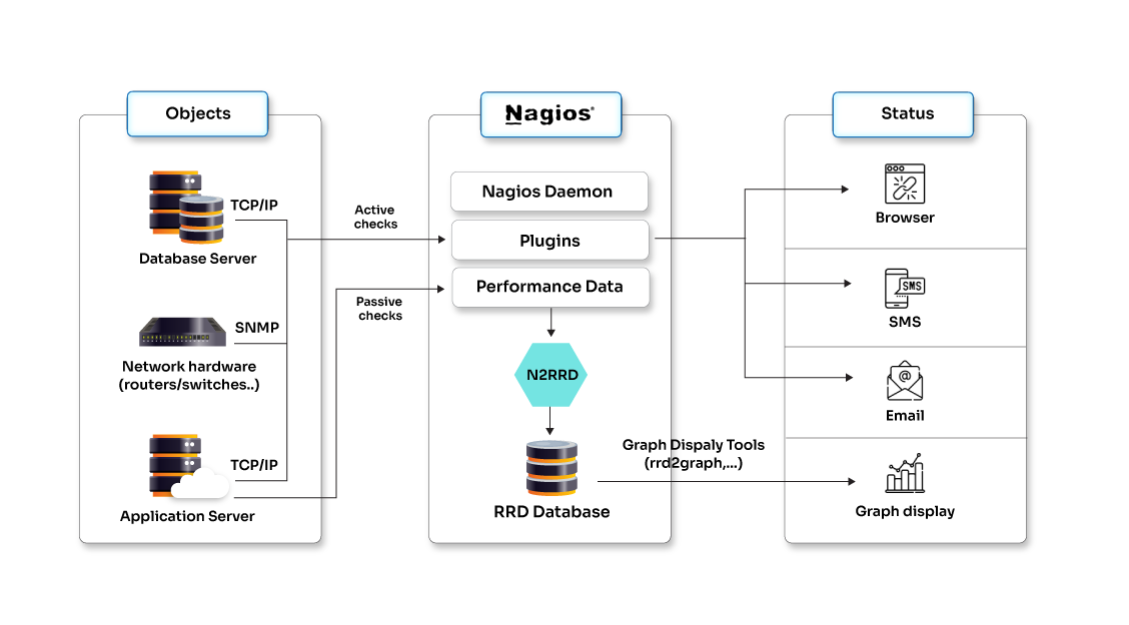
The customer is a supply chain management organization with a substantial on-premises IT setup consisting of several servers, networks, and applications. They remained steadfast with their on-premises infrastructure due to regulatory constraints and business-specific requirements. This led to frequent downtimes and system failures. There needed to be an efficient system to detect issues before they escalated, leading to unnecessary productivity and business losses. The IT team struggled with manual monitoring efforts and could not proactively manage their infrastructure. Opcito's SecOps experts identified Nagios - a leading infrastructure monitoring tool, as a potential solution. Its robust monitoring capabilities, open-source nature, and broad community support were why it was implemented.
Technologies
- Nagios
- Protocols (TCP/IP, SNMP)
- RRD Database
Benefits
- Improved infrastructure management and uptime
- Reduced manual monitoring
- Cost saving
Subscribe to our feed
Educating and empowering developers to build the DevSecOps culture
Educating and empowering developers to build the DevSecOps culture
In our increasingly interconnected world, where data breaches and security threats dominate headlines, it is time for organizations to step up their security game to ensure threats and breaches are kept at bay. To tackle these challenges head-on, it is crucial to establish a robust security culture that penetrates every aspect of an organization.
Mastering dynamic icon colors: Harnessing SVG in React
Mastering dynamic icon colors: Harnessing SVG in React
Ever wished you could change the color of your SVG icons on the fly without bloating your React app? This blog explores how to harness the power of SVGs in React to achieve dynamic icon colors, keeping your application sleek and lightweight.
9 Best practices to master compliances with DevSecOps
Nine best practices to master compliances with DevSecOps
In today's digital landscape, regulatory compliance is no longer a mere checkbox but a critical pillar for organizations striving to build trust and ensure data privacy. Compliance is the cornerstone of a robust security framework, safeguarding sensitive data, protecting customer privacy, and mitigating cyber threats.
All about AWS Inspector-2 for EC2 and how to intentionally generate Inspector-2 findings
All about AWS Inspector-2 for EC2 and how to intentionally generate Inspector-2 findings
Worried about vulnerabilities lurking in your EC2 instances? Fear not! This blog dives deep into AWS Inspector 2, a powerful tool for continuously scanning your EC2 environment, helping you identify and address security risks proactively. Learn how Inspector 2 works, the types of findings it generates, and even how to intentionally trigger findings for testing purposes!
Beyond reactive measures: Harnessing threat modelling for DevSecOps success
Beyond reactive measures: Harnessing threat modelling for DevSecOps success
In the world of software development, DevOps aims to make the process faster and deliver better-quality software to users. DevSecOps takes it a step further by focusing on security, quality, and speed. While tools and tests are in place to ensure the security of the code and configurations, these measures often miss addressing security issues related to how the application is designed and built.