Fortify Your DevOps: Mastering Vulnerability Management
The widespread impact of the CrowdStrike outage has forced businesses to reevaluate their cybersecurity strategies. Luckily, the incident didn't breach any systems, but it revealed the fragility of even the most sophisticated security infrastructures and emphasized the critical nature of proactive vulnerability management systems. Vulnerabilities can cause severe damage to organizations as well as users.
How to enhance Kubernetes security by migrating from Pod Security Policies to Pod Security Admission Controller
Pod Security Policies (PSPs) are a cluster-level resource in Kubernetes that controls security-sensitive aspects of pod specifications. For years, they've served as the cornerstone of security enforcement in Kubernetes clusters by ensuring only pods adhering to specific criteria like running as a non-root user, not running privileged containers, and more are deployed, minimizing vulnerability risks. However, after the release of Kubernetes 1.26, PSPs became deprecated, paving the way for a more robust and flexible approach: the Pod Security Admission Controller.
QA, Performance, and Issue Management for an Investment Management Platform
See how Opcito optimized QA, Performance, and Issue Management for an Investment Management Platform
Engagement details
Opcito partnered with a leading North American investment management platform to address critical performance, security, and reliability challenges. The platform, designed to streamline private equity and venture capital investing for both Limited Partners (LPs) and General Partners (GPs), was overburdened by a growing user base and the sensitive nature of the data it handled. To ensure the platform's continued success, Opcito implemented a comprehensive quality assurance strategy.
Technologies
- JMeter
- Selenium
Benefits
- Enhanced app efficiency
- Improved reliability and stability
- Increased user satisfaction
Subscribe to our feed
The CrowdStrike conundrum
A rainy Friday morning took an unexpected turn when a system failure announcement disrupted my usual pre-flight routine at the airport. At first, I didn't realize the extent of the issue, but then notifications started flooding in, making it clear that this was not just a problem for me but a full-blown worldwide technological crisis. The thought of unexpectedly having my Friday off seemed spectacular, but with their intricate systems and tight schedules forcing airlines to cancel flights, I soon started pondering its broader implications.
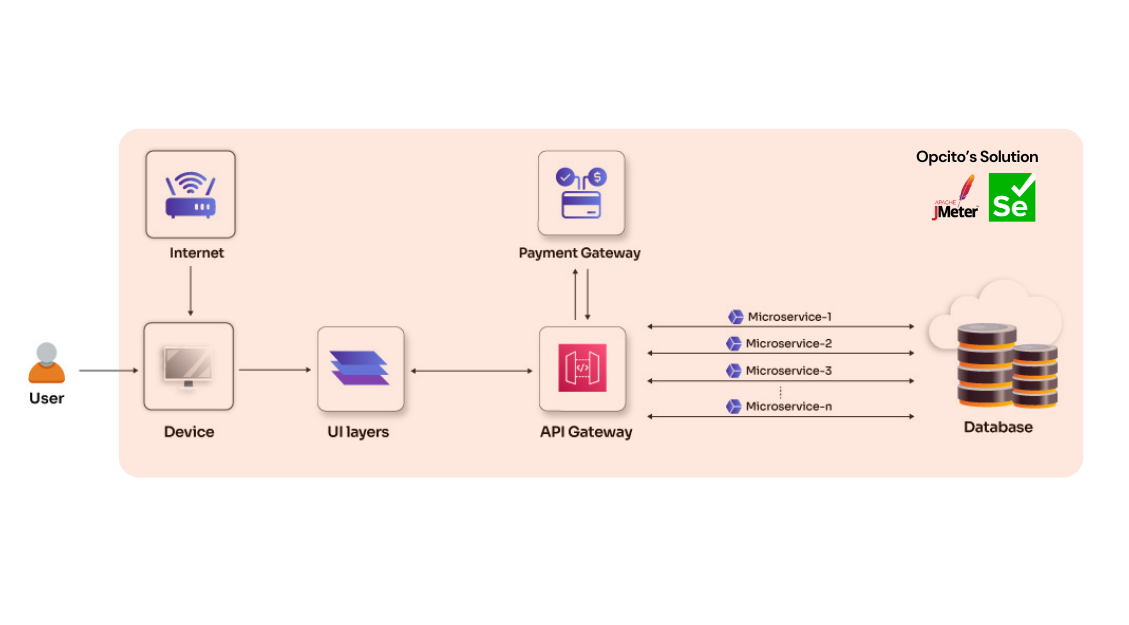
Optimizing performance and scalability by rearchitecting traditional web and mobile applications
See how Opcito optimized performance and scalability by rearchitecting traditional web and mobile applications
Engagement details
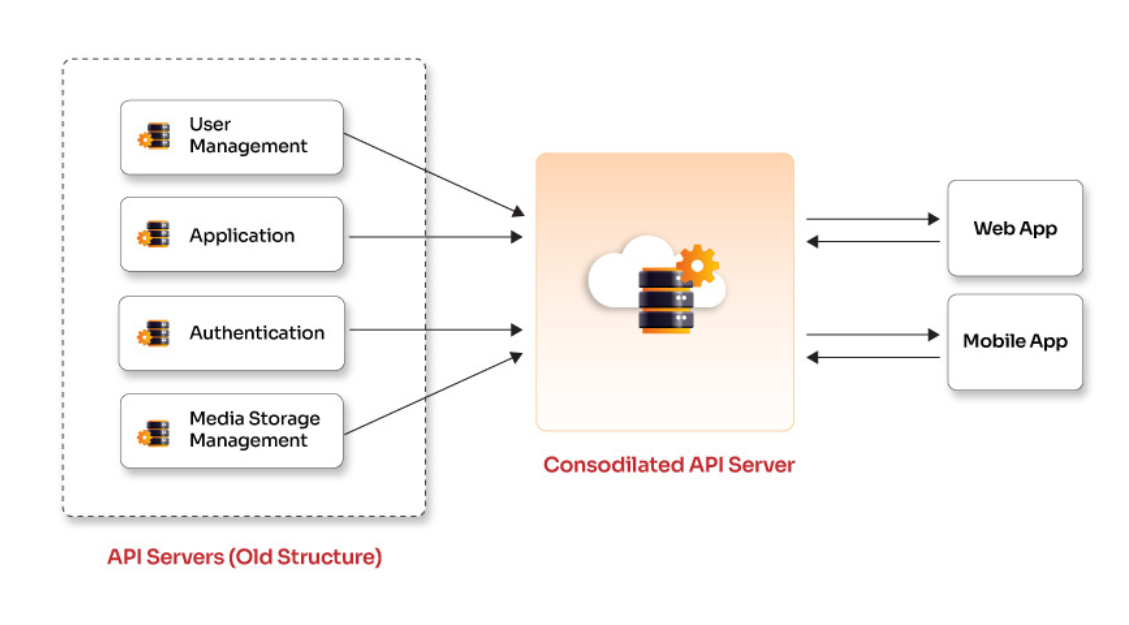
Opcito collaborated with a leading software development company delivering custom IT solutions. The customer's complex web & mobile apps caused performance issues, maintenance headaches, and hindered growth. They need a simpler, more scalable solution. Opcito revamped the customer's app by streamlining data handling and architecture. Opcito redesigned the apps and implemented advanced caching, load balancing, and microservices for smooth performance. Robust APIs were built for easy data exchange, and security was bolstered with real-time data sync and automated validation. Finally, a modern framework using PHP 8 ensured a future-proof foundation with improved performance.
Technologies
- Laravel
- MySQL
- AWS S3
Benefits
- Enhanced performance
- Improved architecture
- Enhanced code quality
- Easy application management
Subscribe to our feed
Exploring real-time communication in Vue.js with Socket.IO
In the fast-paced world of web development, creating applications that offer real-time features is no longer just a luxury—it's a necessity. Whether it's facilitating live chat, collaborative editing, or delivering instant updates, the demand for bidirectional communication between clients and servers is more prevalent than ever. This is where Socket.IO, a powerful library for real-time communication, comes into play. In this blog post, we'll embark on a journey to seamlessly integrate Socket.IO with Vue.js, creating a dynamic and responsive real-time application.
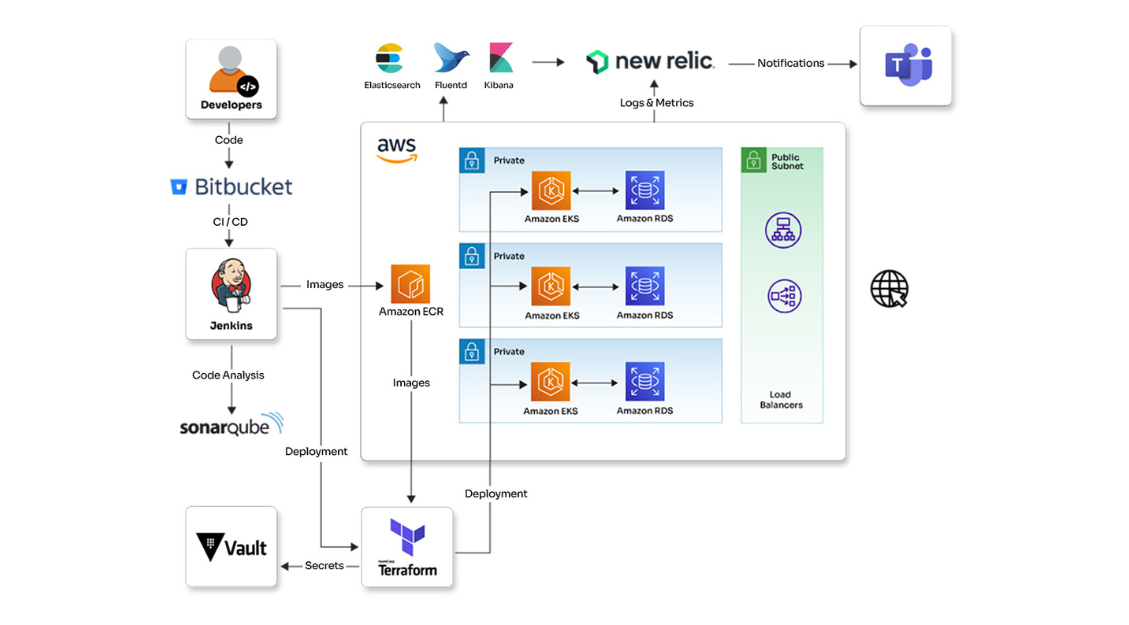
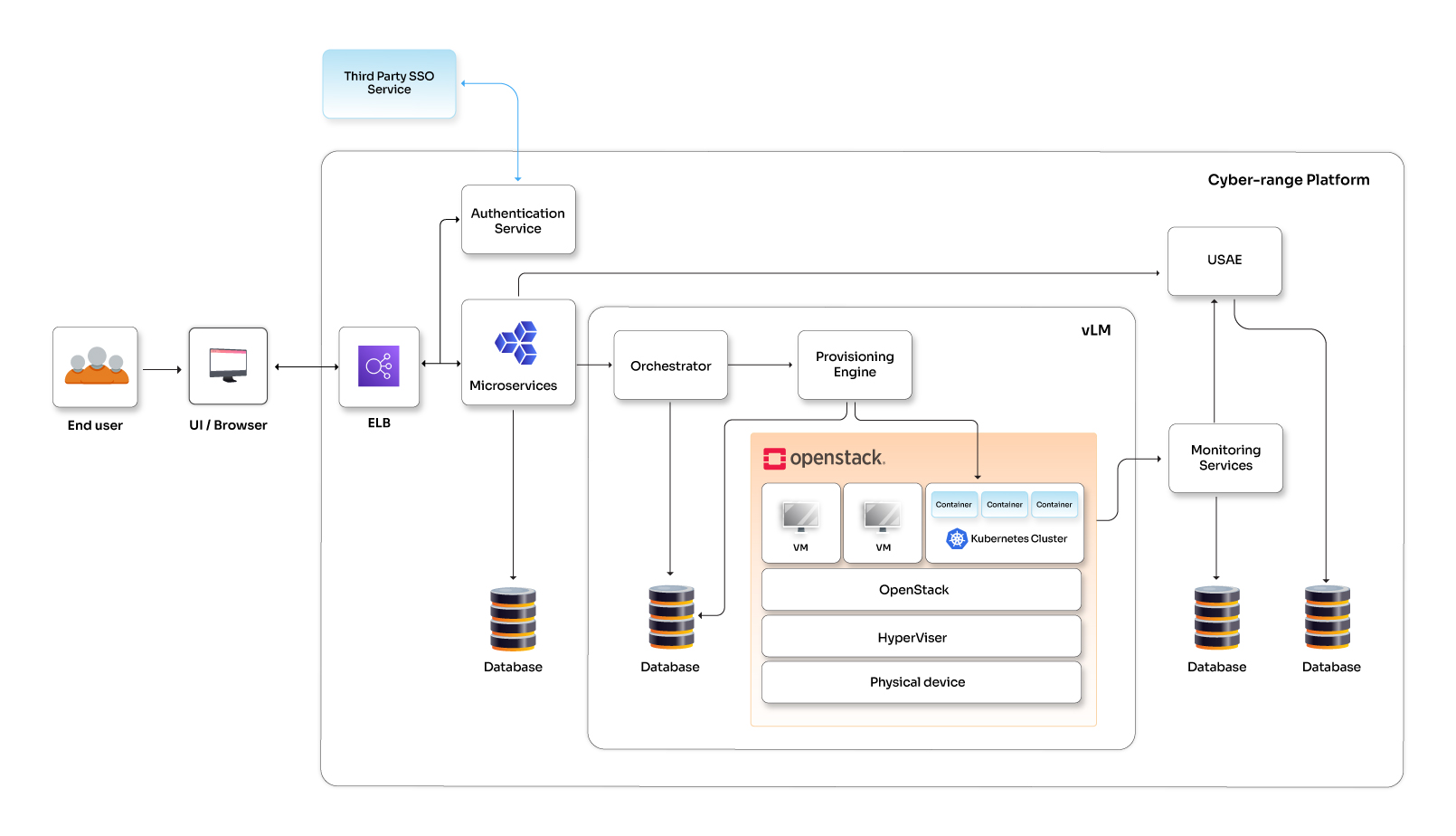
Infrastructure, security, and test automation for a cyber-range platform
See how Opcito enhanced the infrastructure, security, and test automation for a cyber-range platform
Engagement details
Opcito collaborated with a cloud and cyber security expert, to build a secure and scalable cyber-range platform. The customer's platform lacked automated infrastructure and robust CI/CD practices, hindering development and deployment. Opcito implemented DevOps principles to streamline infrastructure provisioning, configuration management, and CI/CD pipelines. Additionally, Opcito integrated monitoring and security practices, enhancing the customer's ability to detect and resolve issues while ensuring code and infrastructure security. The result: a robust, secure platform enabling faster development cycles and improved operational efficiency.
Technologies
- New Relic
- EFK (Elasticsearch, FluentD, Kibana)
- OpenStack
- Terraform
- Ansible
- Python
- SonarQube
- Kubernetes
- Jenkins
Benefits
- Better monitoring
- Higher speed and reliability
- Boosted security
Subscribe to our feed
Ethical implications of AI in software development: A call for responsible innovation
As a passionate advocate for innovation in software development, I've witnessed the transformative potential of Artificial Intelligence (AI) firsthand. AI has rapidly evolved from a theoretical concept to a practical tool capable of automating tasks, optimizing code, and personalizing user experiences. It's poised to become an invaluable asset in the developer's world. However, this immense power must be harnessed responsibly to ensure ethical development and implementation within software.
Developing Custom Terraform Plugins
Terraform empowers you to automate infrastructure provisioning across various cloud platforms, streamlining your workflow. But what if your needs extend beyond these built-in functionalities, and your infrastructure relies on a unique API? Here's where custom Terraform providers come to the rescue!
A Guide to Progressive Web Apps (PWAs)
The way we access the internet has completely transformed in recent years. Mobile browsing has skyrocketed, with smartphones becoming our go-to devices for everything from checking news to shopping online. But this shift has exposed a major problem: traditional websites often struggle to keep up. Imagine waiting ages for a webpage to load, dealing with clunky navigation on a small screen, or missing out on features because you haven't downloaded an app. That's the frustration users face with traditional websites on their smartphones.