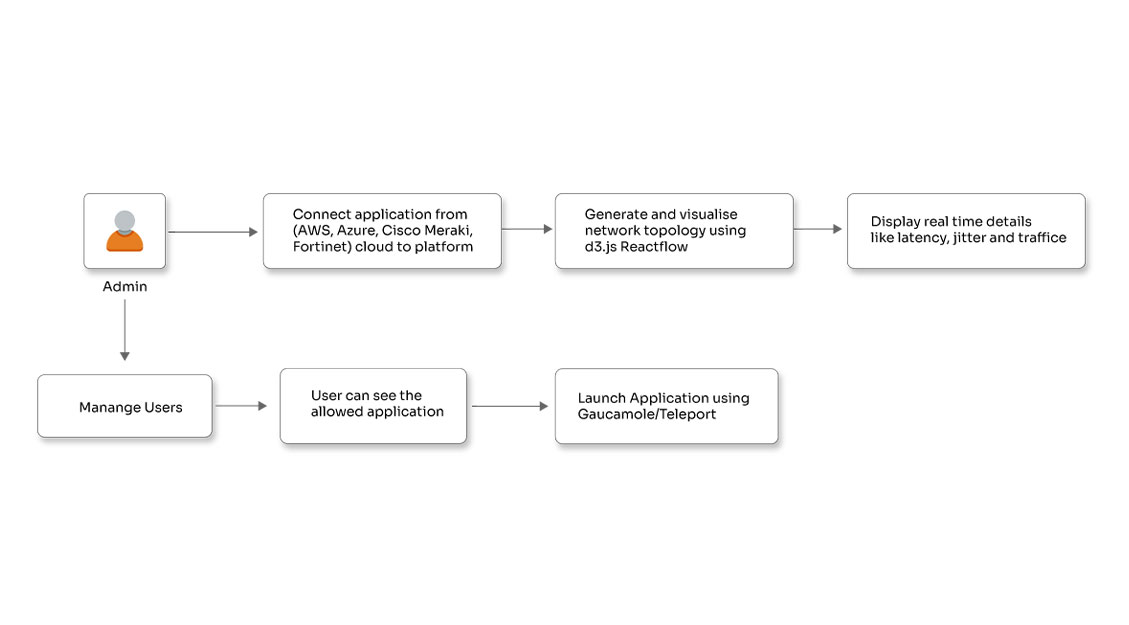
Getting your security posture right is the most important aspect of any IT environment management. The threat landscape and the attackers are evolving every day and it demands innovative cybersecurity solutions. Opcito’s cyber security expertise plays a crucial role in assessing security aspects and ensuring there is no scope for improperly secured digital assets. Our security services, while ensuring complete security, ensure the required business agility and continuity.
Opcito offers comprehensive cybersecurity services that help organizations navigate this evolving threat landscape. Our holistic approach addresses critical areas such as identity and access governance, data protection, risk and compliance, threat management, and cyber security monitoring. By leveraging advanced technologies like automation, machine learning, and artificial intelligence, we provide proactive threat detection and mitigation, enabling organizations to maintain a strong security posture in today's digital age.
EXPERTISE GUARANTEES
Our team of certified cybersecurity professionals has years of experience in identifying and mitigating vulnerabilities and providing security services that you can rely on.
A structured approach to complete security assessment, threat detection, response, and prevention, ensuring comprehensive coverage and timely results.
Dedicated teams for automation of your security needs with expertise in utilization of AI and ML security platforms and services for complete security management.
Fortification of your data, network and infrastructure security, by safeguarding sensitive information and preventing unauthorized access and implementing robust security measures
Our expertise in governance, risk, and compliance (GRC) ensures that your security measures are aligned with industry standards and best practices, while also promoting a culture of security through targeted training and education programs
assets, data, applications, processes, and infrastructure
with cybersecurity services.
End-to-end evaluation of your organization’s security posture with full-scale security assessment of hardware, software, network, configurations, processes, practices, and IT ecosystem by finding security gaps and providing a complete risk mitigation plan.
penetration testing
Enhance your security posture with our time-tested VAPT processes and services, such as network vulnerability scanning, web application penetration testing, mobile application penetration testing, infrastructure penetration testing, and red teaming.
Identify, analyze, and respond to cyber threats in real-time with proactive defense against cyber threats using advanced threat detection, incident response & recovery, security monitoring & alerting, and vulnerability management.
(HIPPA, SOC2, ISO)
Meet your industry specific compliances easily with the help of our compliance expert & tested services such as regulatory compliance assessment, policy & procedure development, and risk assessment & management.

Let our Chief Information Security Officers (CISO) take command of your security programs to ensure the development, implementation, and enforcement of security policies that protect your digital assets effectively, manage disaster recovery and business continuity plans.