A guide to PostgreSQL Indexing with SQLAlchemy
Effective database indexing is paramount for ensuring efficient data retrieval and minimizing query execution times. PostgreSQL, a leading relational database management system, provides a comprehensive set of indexing functionalities. This guide explores leveraging SQLAlchemy, a robust Python library for SQL interaction and Object-Relational Mapping (ORM), to create and manage these indexes within your PostgreSQL environment.
Microfrontend – What is it and what are its benefits?
Monolithic applications have been the backbone of web development and offered a simple way to build applications for years. However, as features piled on, monolithic codebases became a nightmare to maintain, slowed deployments, and limited scalability. That's where microfrontends came into the picture, offering a revolutionary approach to building complex UIs. By breaking down the UI into independent, feature-focused applications, microfrontends today offer a modular and scalable solution.
Fortifying your React application: A guide to common threats and prevention strategies
React has taken the web development world by storm, making building dynamic and engaging user interfaces more accessible. But with this power comes the responsibility for heightened security in React applications. Malicious actors are constantly looking for vulnerabilities, and so it becomes crucial to safeguard React projects from attacks. This article will delve into the numerous security vulnerabilities that React applications and React native apps may encounter and present extensive solutions, best practices, and examples to strengthen the codebase.
Secrets management: The critical piece in your DevSecOps puzzle
Think of the secret ingredients that make your applications work – API keys, database passwords, certificates. These digital credentials unlock access to sensitive data and functionalities, but keeping them secure can be challenging. A recent study by Gartner found that by 2027, 70% of organizations will combine data loss prevention and insider risk management disciplines with IAM context to identify suspicious behavior more effectively.
Feign Client: Powerful and clean Spring Boot APIs
Building microservices is a powerful approach, but interacting with external APIs often becomes repetitive. Developers using RestTemplate must write code for every step, from building URLs to handling responses, leading to a slow process that is error-prone and, frankly, frustrating. Fortunately, there is a better way to handle this problem and help developers manage large amounts of API calls—using the Feign Client in Spring Boot. This blog will explain how the Feign Client in microservices streamlines Spring Boot API interactions.
The art of security in software development: Opcito approach
Imagine millions of users' credit card details and personal information exposed because of a security flaw. Unfortunately, this isn't a hypothetical scenario. In 2017, Equifax, a major credit bureau, suffered a data breach that impacted a staggering 147 million Americans. This incident, and countless others like it, highlighted a critical failing in software development - the afterthought approach to security. But what if we built security into the very foundation of our software, from the first line of code to deployment and delivery?
Custom Hook in React to solve useEffect double invocation
Functional components are taking center stage in React development, thanks partly to the streamlined useEffect Hook. It handles tasks like data fetching and local storage much more elegantly than lifecycle methods in class components. But there's a hidden shortcoming. useEffect can fire twice unexpectedly, potentially harming your app's performance. This blog post explores this challenge and provides clear solutions for effectively managing side effects using useEffect in React applications.
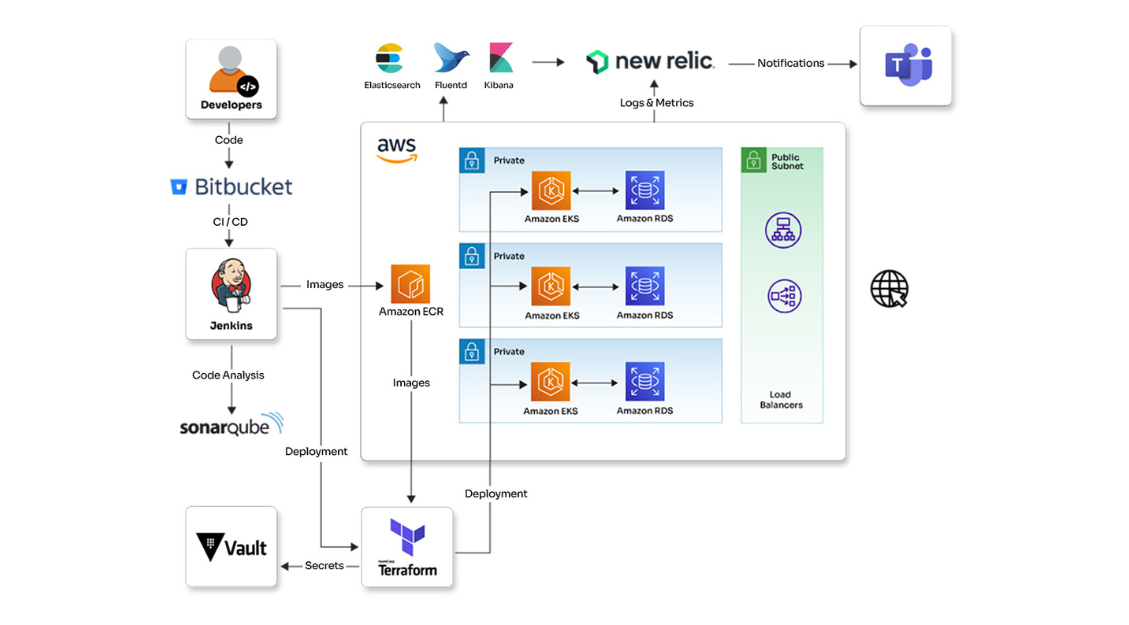
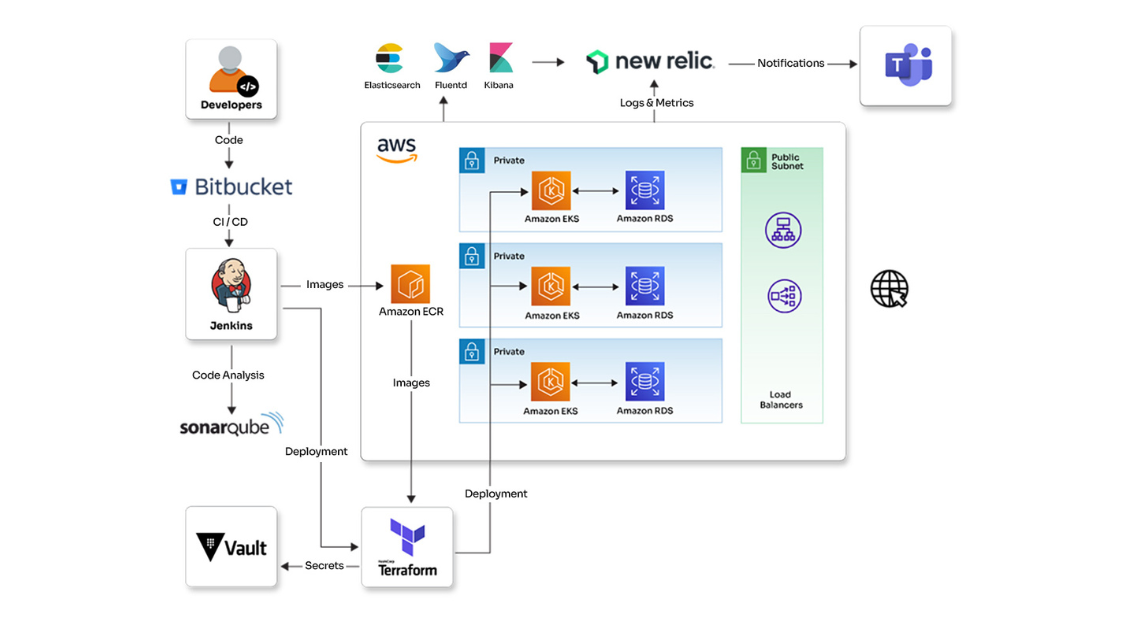
Enhanced infrastructure automation and monitoring incident management solution for a healthcare organization
See how Opcito enhanced infrastructure automation and incident management monitoring solutions for a healthcare organization
Engagement details
Opcito partnered with a digital healthcare organization to improve their web application's efficiency and scalability. The healthcare organization lacked automation and monitoring for their infrastructure, making it difficult to manage. Opcito implemented Site Reliability Engineering (SRE) practices to address these issues. This collaboration improved the organization's ability to monitor their system, automate tasks, and plan for future growth. The improvements resulted in a more reliable and efficient web application.
Technologies
- New Relic
- EFK
- AWS cloud
- Terraform
- Ansible
- Python
- SonarQube
- Kubernetes
- Jenkins
Benefits
- Better monitoring
- Optimized disaster recovery
- Higher speed and reliability
- Boosted security
Subscribe to our feed
AISecOps: The future of security operations is intelligent
The digital landscape is constantly evolving, and so are the threats we face. Traditional security operations, reliant on manual analysis and limited resources, need help to keep up with the ever-growing volume and sophistication of cyberattacks. This is where AISecOps steps in, offering a revolutionary approach that leverages the power of Artificial Intelligence (AI) and Machine Learning (ML) to transform security operations.
Step-by-step guide to VPC peering
Step-by-step guide to VPC peering
Have you ever built a cloud application that uses multiple Virtual Private Clouds (VPCs) in AWS? But then a question arises – what if these isolated VPCs need to interact with each other privately, without compromising security? This is where VPC peering comes to the rescue. In this blog, we'll delve into the world of VPC peering and explore how it establishes a secure, private network connection between your VPCs, acting as a dedicated bridge within the AWS cloud.