How to write Ansible Roles and publish them on Ansible Galaxy?
How to write Ansible Roles and publish them on Ansible Galaxy?
Configuration management is one of the key areas when it comes to maintaining a fast-paced, agile, and continuous development environment. I am mentioning fast-paced because you can see the number of software and hardware updates you get day in, day out. Even the smallest of devices, like your mobile phones, get a system update every year. Your source code or library needs a patch fix; your operating systems get updates from time to time, and your firewalls and firmware need an update.
Build your CI/CD with AWS CodePipeline and Elastic Beanstalk
Build your CI/CD with AWS CodePipeline and Elastic Beanstalk
DevOps is fast becoming a standard right now and CI/CD (Continuous Integration and Continuous Delivery/Deployment) is the term often associated with development and release of a software in the DevOps process. In simple terms, CI (Continuous Integration) is a process that allows developers to integrate their code in the main shared repository, multiple times a day and providing them with instant feedback about possible broken functionality or tests.
Kickstarting your Node.js with Spanner
Kickstarting your Node.js with Spanner
Node JavaScript or Node.js is an open source, cross-platform, runtime environment for executing JavaScript code outside a browser. Node.js is often used to build back-end services which are nothing but the APIs. A backend is an application running on a server or on the cloud to store data, send emails or push notifications, and kick off workflows. Node.js is ideal for building highly scalable data-intensive and real-time back-end services that can boost your applications. Also, if required, the backend can serve to the backend.
KubeVirt – An Initial Look
KubeVirt – An Initial Look
Kubernetes is a great solution when you want to run container workloads. The options and flexibility it affords you let you run your applications within containers with ease. This is great when you have applications that are easily containerized. But what if you have applications that aren’t easily containerized (legacy applications, enterprise software), but you’d still like to leverage the features that Kubernetes gives you?
The classic dilemma for testers - Robot or pytest
The classic dilemma for testers - Robot or pytest
For any organization, customer confidence is of the highest priority, and a lot of it is dependent on reliability which is mostly dependent on the quality assured by the product and service you are providing. This has increased the importance of QA, Testing teams and the framework you are using for testing. Choosing the right test framework for a project is a critical decision.
Integrating Django with Salesforce
Integrating Django with Salesforce
Salesforce is a customer success platform with their CRM solution leading the CRM market for a considerable time. Salesforce offers many Services(SaaS) and Products(PaaS) which aid in the efficient functioning of organizations by providing smoother integration between various departments. Salesforce offers a range of features in functional areas of a company, including sales, marketing, customer support, team performance data, etc., and has proven itself as an indispensable tool.
From the CEO’s Desk: DevOps with Microsoft Azure part 2 - VSTS and TFS
DevOps with Microsoft Azure part 2 - VSTS and TFS
In my last blog, I talked about “how Microsoft is trying to change its perception in the open source world and how the recent acquisitions are making it a formidable force in the DevOps space?” I mentioned the services from Microsoft Azure that are cementing its position as a DevOps amicable technology.
Kubernetes 1.11 – What to look forward to?
Kubernetes 1.11 – What to look forward to?
Kubernetes 1.11 is the second release of the container orchestration platform this year. This release continues to expand on the themes of maturity, flexibility, and scalability. It does look like the team has been hard at work after the last release, with key features in the networking sphere graduating to stable (CoreDNS plugin + In-Cluster Load Balancing) along with some exciting features being released to beta from the API Machinery and Node SIGs.
Optimizing data pipeline using Big Data analytics techniques
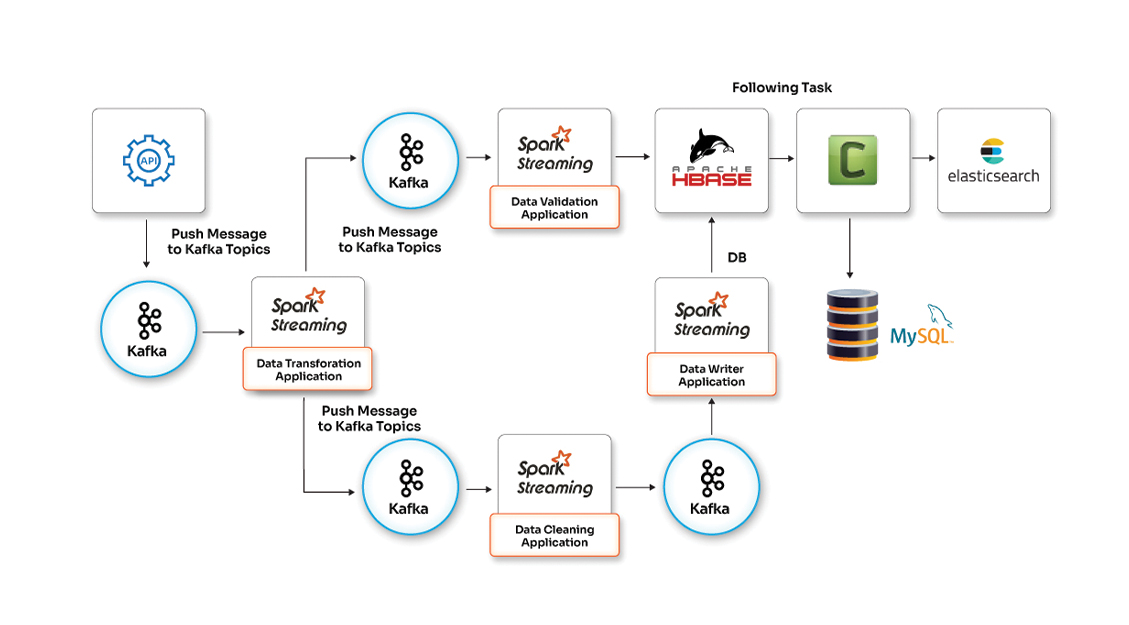
See how Opcito optimized data pipelines using Big Data analytics techniques
Engagement details
A product that uses data transformation and data processing activities to produce results can be hard to manage. The time consumed to process data sequentially using a traditional framework consisting of MySQL could be a problem that can increase the time to process data and produce results.
Technologies
Big Data
Tools and platforms
- Apache Kafka
- Spark
- HBase
- MySQL
Benefits
- Faster delivery with the ability of parallel data processing
- Performance optimization with the gilt-edge utilization of the computing power/resources
Subscribe to our feed
Microservices deployment strategies on Kubernetes
Microservices deployment strategies on Kubernetes
Kubernetes provides a very advanced platform for making continuous deployment a reality for software development teams. Continuous deployments and delivery take away the dread and crunch associated with deploying new code to users. The ability to reliably deploy code and, more importantly, rollback when problems occur is invaluable to fast-moving development teams. This gives engineering teams the flexibility to experiment while iterating very fast.