Exploring Network Security with Nmap

Posted By
Siddharth Sharma

In our interconnected world, safeguarding data and systems from potential threats is fundamental, and network security plays a pivotal role in achieving this goal. Understanding your network and identifying vulnerabilities is a fundamental step in ensuring robust security measures. This is where Nmap comes into play.
What is Nmap?
Nmap, short for Network Mapper, is a versatile and powerful open-source network scanning tool designed for network discovery, security auditing, and vulnerability assessment. It allows users to probe networks, discover hosts, open ports, and gather information about the services running on those ports.
Why is Nmap required?
Let’s look at the uses of Nmap
- Network discovery: Nmap helps network administrators and security professionals discover devices and hosts on a network. It can scan a range of IP addresses and provide a list of active hosts, which is essential for network management and security audits.
- Service detection: Nmap can identify the services and open ports on remote systems. This information is crucial for understanding what services are running, which versions are in use, and potential vulnerabilities that need to be addressed.
- Vulnerability assessment: We can use Nmap to detect vulnerabilities in networked systems. By identifying open ports and the services running on them, administrators can determine which systems might be vulnerable to attack and take appropriate measures to secure them.
- Network mapping: Nmap can create network maps that visualize the structure of a network, including routers, firewalls, and connected devices. This helps in network design and documentation.
- Security audits: Nmap is a valuable tool for security audits and penetration testing. It can be used to assess the security of a network by identifying potential weaknesses and entry points that malicious actors could exploit.
- Troubleshooting: We can use Nmap to diagnose network issues and connectivity problems. By scanning a network and checking which services are running, they can quickly identify the source of problems.
- Open source and extensible: Nmap is open-source software, which means it is freely available and can be customized to suit the specific needs of an organization or individual users. It has a large community of users and developers who contribute to its functionality.
This guide will take you on a journey through the world of Nmap and help you understand it better.
What are the steps to install Nmap
We will use the Linux OS to install the Nmap tool, but you can use any OS like Ubuntu, Red Hat, Centos, or Amazon Linux. Follow this link to download the tool from the official website: https://nmap.org/download
In this scenario, we're going to use the Red Hat OS
For Ubuntu:
apt-get update && apt-get install nmap –y
For Red Hat and CentOS:
yum update && yum install nmap –y
When you hit the above command, the output will be like below:
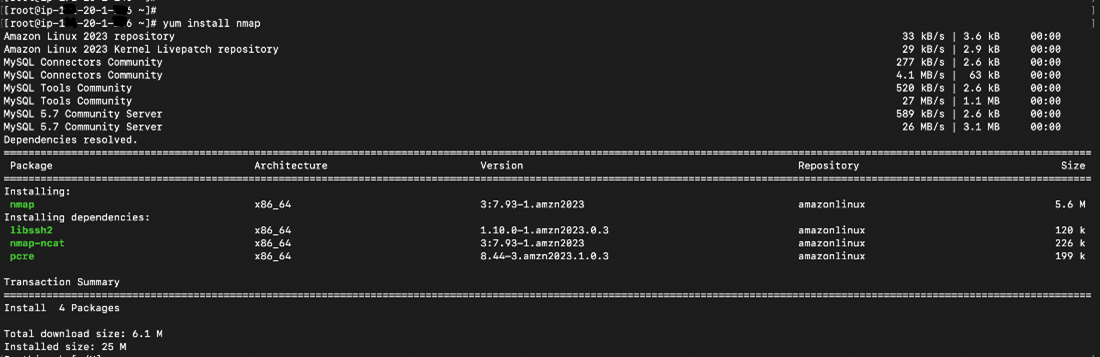
Key features of Nmap
Nmap boasts several key features that make it a go-to choose for network reconnaissance:
1. Port Scanning: It is a technique to identify open ports on a target host. It's a valuable tool for security professionals to assess the security of a network. It excels at scanning and identifying open ports on target hosts.
To conduct a basic multiple port scan using Nmap, you typically provide the target host or IP address as an argument with –p filter. Here's a simple example where are scanning the port from 22 to 33 on the target.

TCP SYN Scan (Stealth Mode scanning):
nmap -sS target_host_or_ip
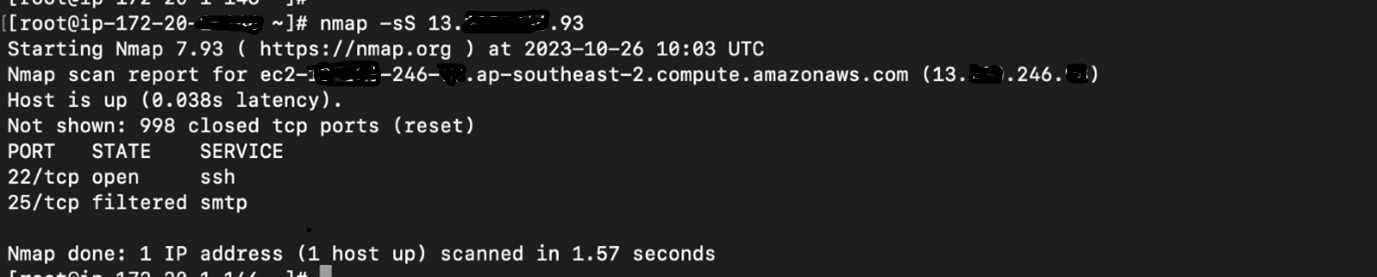
UDP Scan:
nmap -sU target_host_or_ip

Full TCP Scan (All ports):
nmap -p- target_host_or_ip

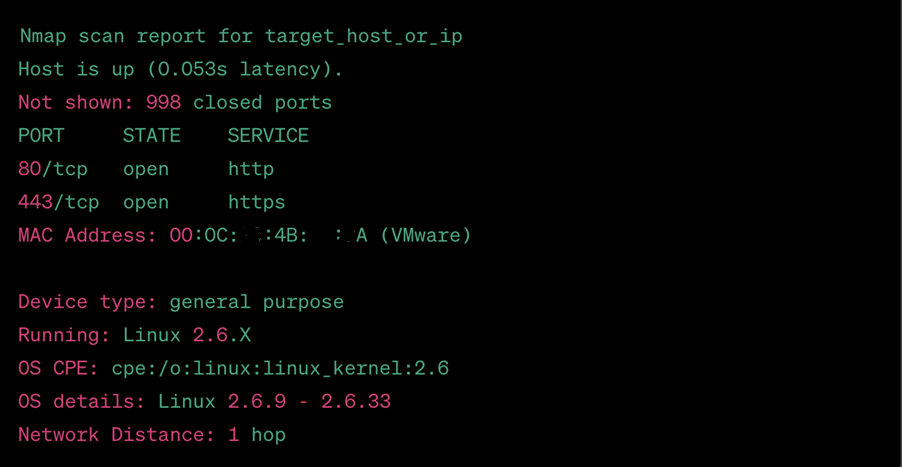
2. OS Detection: Nmap can perform operating system (OS) detection as part of its network scanning functionality. OS detection is a valuable feature because it helps identify the specific operating system running on a target host.
Here is an example of how to use Nmap to perform OS detection:
nmap -O target_host_or_ip
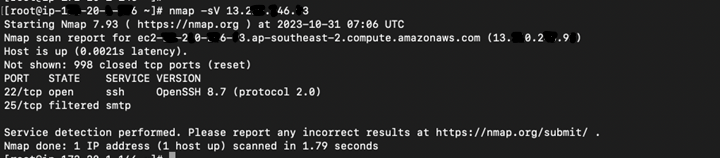
3. Version Detection: It can also identify specific versions of services running on open ports. Check the below command as it is showing the version for ssh service in the snap.
nmap -sV target_host_or_ip
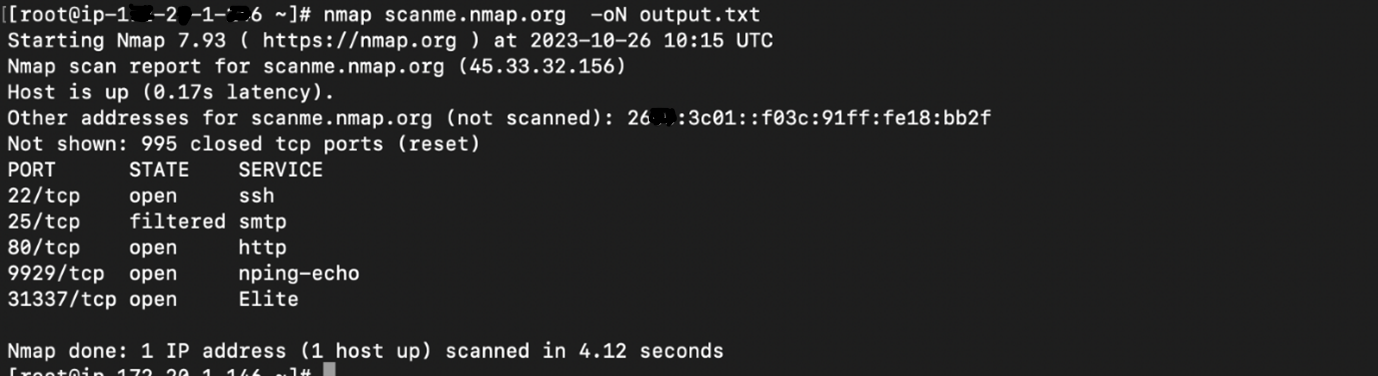
4. Output to file: Nmap provides different output formats, including text, XML, and Grepable, allowing users to choose the format that suits their needs best. Check the below command as per your requirement.
For txt:
nmap scanme.nmap.org -oN output.txt
For XML:
nmap scanme.nmap.org -oX output.xml
5. Disabling DNS name resolution: We can disable DNS name resolution in Nmap using the -n option. This is useful when you want to speed up your scans by skipping DNS lookups. Here's an example of how to use the -n option in Nmap
nmap -n target_host_or_ip

By disabling DNS resolution, your scan may run faster, especially when dealing with targets that do not have DNS records associated with their IP addresses. This is particularly useful when you prioritize scan speed over obtaining hostnames in your Nmap results.
Extra-Tips for using Nmap:
- Use the -Pn option to skip the ping scan. This can be useful for scanning networks where you know that all of the hosts are online.
- Use the -sT option to perform a TCP connect scan. This type of scan is more thorough than a SYN scan, but it is also more likely to be detected by firewalls and intrusion detection systems.
- Use the nmap –sP command which locates machines, make sure that machines are responding, or identifies unexpected machines across a network.
- Use the -F option to perform scanning on common ports of the network.
- Use the -A option to perform a comprehensive scan. This will include all the scan types listed above, as well as additional tests to identify operating systems and vulnerabilities.
- When using Nmap, it is essential to be respectful of other networks. Avoid scanning networks without permission and be careful not to overload networks with traffic.
Conclusion
Nmap is a cornerstone of network security and an indispensable asset in today's interconnected landscape. Its value lies in its different capabilities that empower individuals and organizations to fortify their digital domains. It offers a profound understanding of the network, unveiling its architecture and potential weaknesses. By identifying open ports and performing OS and version detection, Nmap equips developers with the knowledge to secure networks proactively.
Nmap also excels in troubleshooting network issues. Its ability to swiftly diagnose problems by revealing open or closed ports, as well as the status of essential services, minimizes downtime and streamlines maintenance. That's why it proves so essential for ethical hackers and security professionals. Go ahead, try it, and experience the power of the Network Mapper in securing your network and enhancing your cybersecurity skills.
Related Blogs




















